Table of Contents
Home / Blog / Web Development
Understanding Web Authentication: Methods, Protocols, and Best Practices
March 24, 2025

March 24, 2025
Website authentication is essential for securing online platforms, protecting user data, and preventing unauthorized access.
As cyber threats evolve, robust authentication methods have become a necessity rather than an option. Notably, 81% of corporate data breaches have been attributed to poor password practices.
Despite this alarming statistic, multi-factor authentication (MFA) adoption remains low, with 65% of global small and medium-sized businesses (SMBs) not utilizing MFA and lacking plans to implement it. This highlights the critical need for organizations to adopt secure, efficient, and user-friendly authentication solutions to protect their systems and data effectively.
In this article, we will talk about web authentication, how it works, its benefits, different types, common web authentication methods, and protocols. Not just that, we will discuss web authentication best practices and a step-by-step implementation guide.
Weak Logins Won’t Cut It—Let’s Fortify Your Security!
Our advanced web authentication solutions ensure only the right users get in while keeping cyber threats out. What’s stopping you from taking the first step toward a safer website?
What is Web Authentication?
Web authentication (or web auth) is a security mechanism used to validate a user’s identity before allowing access to web-based services, applications, and data. This ensures that only authorized individuals can access a system, thereby preventing unauthorized access, fraud, and data leakage. Site authentication can range from classic username-password combinations to more advanced biometric and hardware-based solutions.
How Web Authentication Works
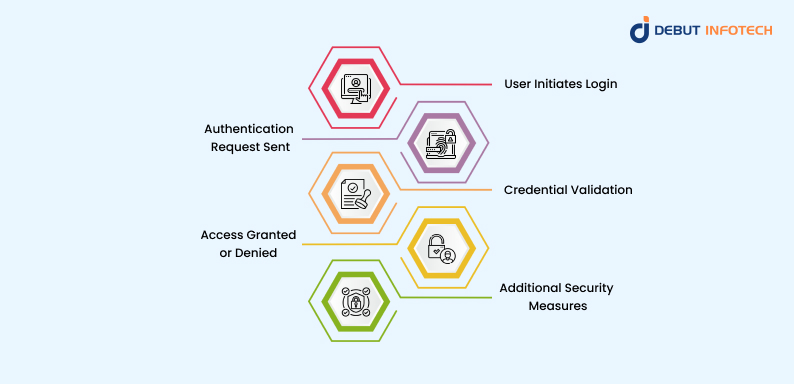
If you have wondered: how does authentication work? Then, you’ve arrived at the right page.
Web authentication typically follows a structured process to verify users securely. Here are the crucial steps :
1. User Initiates Login
The authentication for website process starts when a user provides their credentials (username and password, biometric data or a security token). Other systems securely recognize suspicious login activities, launch extra verification steps, and prevent unauthorized access.
2. Authentication Request Sent
After the user enters their credentials, the system securely sends the authentication request to a server. Secure connection (such as HTTPS) transfers encrypted data, which cannot be intercepted by cyber attackers.
Many top-notch web development companies implement third-party authentication providers for added security.
3. Credential Validation
The server compares the provided credentials against stored records, using hashing and encryption techniques to protect sensitive data. Suppose multi-factor authentication (MFA) is enabled. In that case, the system requests an extra verification step, such as a one-time password (OTP) or biometric confirmation.
4. Access Granted or Denied
If credentials match, access is granted, and the user is redirected to their account dashboard. Failed attempts trigger security measures like account lockouts, CAPTCHA challenges, or alerts to notify the user of possible unauthorized access attempts.
5. Additional Security Measures
To enhance security, some systems implement session timeouts, device recognition, and continuous authentication. These measures ensure users remain authenticated without requiring frequent logins while monitoring for suspicious activity that could indicate credential theft or unauthorized access.
Benefits of Web Authentication
Implementing authentication solutions can reduce web application development cost by preventing security breaches and minimizing user account recovery expenses. Here are some benefits of web authentication:
1. Enhanced Security
Web authentication protects sensitive data by verifying user identities before granting access. Techniques like encryption, multi-factor authentication (MFA), and biometric verification reduce risks associated with brute-force attacks, credential stuffing, and unauthorized access. Continuous monitoring and adaptive authentication further strengthen security in progressive web development environments by detecting unusual login patterns and potential threats in real-time.
2. Improved User Experience
Modern authentication methods, such as Single Sign-On (SSO) and passwordless login, streamline access across custom software development projects, applications, and services. Users no longer need to remember multiple passwords, reducing frustration and login delays. Features like biometric authentication and secure token-based logins enhance convenience without compromising security, leading to a smoother and more efficient authentication process.
3. Reduced Password Management
By implementing secure alternatives like passwordless authentication, token-based logins, and biometric verification, web authentication minimizes the need for frequent password resets. This reduces IT support costs and prevents user frustration caused by forgotten credentials. Automated password policies and secure storage methods further enhance password management without compromising security.
4. Compliance with Security Standards
Many industries must comply with regulations like GDPR, HIPAA, and PCI DSS, which require robust authentication mechanisms. Implementing strong methods of authentication ensures adherence to these standards, protecting user data and avoiding legal penalties. Regular audits, encryption techniques, and identity verification protocols help organizations maintain compliance while enhancing trust and credibility among users.
Different Types of Web Authentication
Various authentication types enhance security while offering flexibility in implementation.
Choosing between authentication methods depends on the use case, whether for a web app vs mobile app. Each has unique security and user experience considerations.
Common types of authentication methods include:
1. Password-Based Authentication
Users enter a unique password linked to their account for verification. While widely used, businesses should invest in rapid web application development tools that support additional layers of security like hashing and salting.
Security measures like hashing, salting, and password managers improve protection. However, weak passwords, credential reuse, and phishing attacks make this method vulnerable without additional security layers like multi-factor authentication (MFA).
2. Multi-Factor Authentication (MFA)
MFA necessitates users to verify their identity using two or more authentication factors, such as a password, security token, or biometric data. This method significantly enhances security, reducing the risk of credential theft, but it may introduce additional login steps for users.
3. Biometric Authentication
Biometric authentication utilizes unique physical or behavioral characteristics like fingerprints, facial recognition, or voice patterns. This approach eliminates password-related risks but requires specialized hardware and raises concerns about biometric data storage, privacy, and potential spoofing attacks using deepfake technology or stolen biometric samples.
4. Token-Based Authentication
This method uses temporary cryptographic tokens, such as JSON Web Tokens (JWT) or OAuth tokens, to authenticate users without requiring repeated password entries. It enhances security and convenience, but session hijacking, token leakage, and improper implementation can lead to security vulnerabilities.
5. Single Sign-On (SSO)
SSO permits users to log in once and access multiple applications without entering credentials again. It streamlines authentication while improving security by reducing password fatigue. However, if the SSO provider is compromised, all linked accounts become vulnerable to unauthorized access.
6. Certificate-Based Authentication
Users authenticate using digital certificates issued by a trusted Certificate Authority (CA). This approach is commonly used in enterprise ecommerce website development projects that require heightened security.
The certificate verifies identity through cryptographic keys, enhancing security and eliminating passwords. While highly secure, managing and renewing certificates can be complex, requiring careful implementation and infrastructure support.
Common Website Authentication Methods
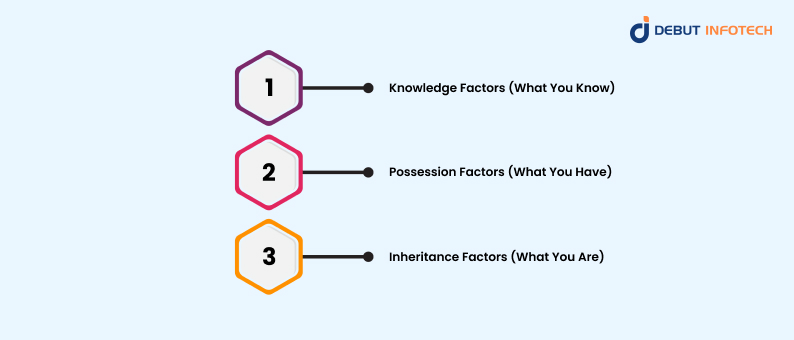
Here are different authentication methods for websites:
1. Knowledge Factors (What You Know)
Knowledge-based authentication requires users to provide information they remember, such as passwords, PINs, or security questions. It is the most traditional form of authentication and is widely used across digital platforms. Users create unique credentials that must be kept confidential to prevent unauthorized access.
Many systems and authenticated websites enhance security by imposing password complexity rules, such as requiring a mix of letters, numbers, and special characters. Some also implement periodic password changes to mitigate risks.
Benefits
- Familiar and easy to implement.
- No additional devices or hardware are required.
- Works across various systems without major adjustments.
Drawbacks
- Vulnerable to phishing, keylogging, and brute-force attacks.
- Users often struggle with remembering complex passwords.
- Password reuse increases the risk of credential compromise.
2. Possession Factors (What You Have)
Possession-based authentication verifies users through physical objects they own, such as security keys, smart cards, or mobile authentication apps. This method enhances security by ensuring that even if a password is compromised, access cannot be granted without the required physical device. One-time passwords (OTPs) sent via SMS or email also fall under this category. However, hardware-based solutions like USB security keys are more secure.
Organizations often use possession factors in combination with knowledge factors for multi-factor authentication (MFA).
Benefits:
- It is more secure than password-only authentication.
- It prevents remote attackers from accessing accounts without the device.
- It enhances MFA effectiveness when combined with other factors.
Drawbacks:
- Users can lose or misplace authentication devices.
- Physical tokens and smart cards may require replacement over time.
- Some methods, like SMS-based OTPs, are vulnerable to interception.
3. Inheritance Factors (What You Are)
Inheritance-based authentication relies on biological traits unique to each user, such as fingerprints, facial recognition, iris scans, or voice patterns. This method offers a high level of security since biometric data is difficult to replicate. Many modern devices, including smartphones and laptops, incorporate biometric authentication for secure access.
Some systems store biometric templates locally to enhance privacy and prevent data breaches. However, biometric authentication must be implemented with encryption and anti-spoofing measures to prevent unauthorized use.
Benefits
- It offers strong security since biometric traits are unique to each user.
- It enhances convenience by eliminating the need for passwords or physical devices.
- It reduces the risk of credential sharing or theft.
Drawbacks:
- Requires biometric-enabled hardware, increasing implementation costs.
- Privacy concerns arise regarding biometric data storage and misuse.
- Biometric systems may fail in certain conditions (e.g., wet fingers affecting fingerprint scanners).
Common Web Authentication Protocols
Several protocols ensure secure web authentication processes. They are:
1. FIDO (Fast Identity Online)
FIDO is an open authentication standard that eliminates password reliance by using cryptographic authentication methods. It supports biometrics, security keys, and device-based authentication, reducing phishing risks. FIDO enhances security by ensuring credentials never leave a user’s device, preventing credential theft and replay attacks.
2. FIDO2
FIDO2 builds upon FIDO by enabling passwordless authentication using WebAuthn and CTAP protocols. It allows users to sign in securely with biometrics or hardware tokens. This protocol strengthens security while enhancing user convenience, reducing password-related vulnerabilities, and simplifying authentication across web applications and mobile platforms.
3. CTAP (Client-to-Authenticator Protocol)
CTAP allows external authenticators, like security keys and biometric devices, to communicate with browsers and online services. It enables strong authentication without passwords by integrating with FIDO2 and WebAuthn. CTAP supports cross-platform authentication, ensuring secure access across various devices and environments.
4. CTAP2
CTAP2 improves upon CTAP by enhancing authentication flexibility and security. It introduces PIN-based verification for additional protection, allowing users to authenticate using biometrics or physical security keys. CTAP2 ensures phishing-resistant authentication and provides a seamless, secure login experience across multiple applications and platforms.
Website Authentication Best Practices
1. Explore Passwordless Authentication
Passwordless authentication enhances security by eliminating traditional passwords, and replacing them with biometrics, security keys, or magic links. This reduces the risk of credential theft, phishing, and password reuse. Implementing FIDO2-compliant authentication methods ensures a seamless, secure login experience while maintaining high levels of user convenience and protection.
2. Encourage Strong Passwords if Used
If passwords remain necessary, enforce complexity rules, requiring a mix of uppercase letters, numbers, and special characters. Encourage users to avoid common words and against reusing them across multiple sites. Implement periodic password changes, breach detection alerts, and password managers to strengthen security and reduce vulnerability to brute-force attacks.
3. Implement Multi-Factor Authentication (MFA)
MFA adds an extra security layer by requiring users to verify their identity through multiple factors, such as OTPs, biometric scans, or security keys. This prevents unauthorized access even if passwords are compromised. Adaptive MFA, which adjusts security levels based on risk analysis, further enhances authentication reliability.
4. Integrate SSO Authentication
Single Sign-On (SSO) simplifies authentication by allowing users to access multiple applications with a single login. This reduces password fatigue and improves security by centralizing authentication management.
A reliable web development company can implement industry-standard SSO protocols like SAML or OpenID Connect, ensuring seamless integration across platforms while maintaining robust access control.
5. Limit Password Attempts and Resets
To prevent brute-force attacks, restrict the number of failed login attempts before temporarily locking an account.
Implement CAPTCHA challenges and email/SMS notifications for suspicious activity. For password resets, enforce identity verification steps, such as OTPs or security questions, to prevent unauthorized account takeovers.
6. Regularly Monitor and Audit Authentication Logs
Monitoring authentication logs helps detect unusual login patterns, failed attempts, and potential security breaches. Implementing real-time alerts for suspicious activity enhances incident response. Routine audits of authentication mechanisms ensure compliance with security policies, identifying vulnerabilities before attackers can exploit them.
7. Secure Authentication Data with Encryption
Protect stored authentication credentials using strong encryption algorithms like AES-256 or bcrypt for password hashing. Ensure encrypted communication channels (TLS/SSL) prevent data interception. Avoid storing plaintext passwords, and regularly update cryptographic protocols to defend against evolving security threats and cyberattacks.
Using robust encryption techniques strengthens the tech stack for web development, ensuring data protection.
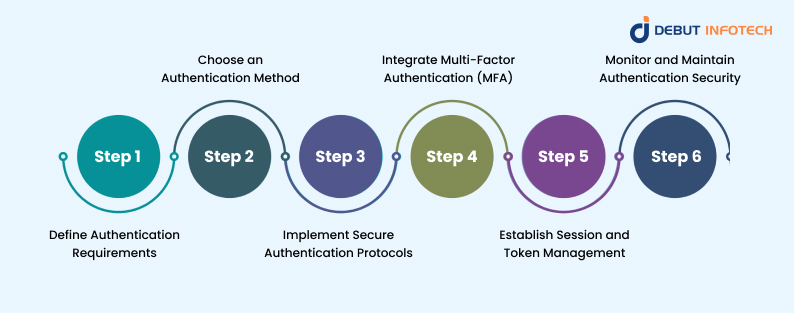
Steps to Implement Website Authentication
1. Define Authentication Requirements
Determine security needs based on user roles, data sensitivity, and compliance regulations. Decide on authentication methods such as passwords, multi-factor authentication (MFA), or biometric verification. Establish policies for password complexity, session management, and user access levels to enhance security while maintaining usability.
2. Choose an Authentication Method
Select an authentication approach that balances security and user convenience. Options include password-based login, single sign-on (SSO), token-based authentication, or passwordless methods. Consider using FIDO2, OAuth, or OpenID Connect to improve authentication security while ensuring seamless integration across different applications and devices.
3. Implement Secure Authentication Protocols
Use industry-standard protocols like OAuth 2.0, OpenID Connect, and FIDO2 to protect authentication processes in web and mobile web app development projects. Encrypt user credentials using hashing algorithms like bcrypt or Argon2. Secure data transmission with TLS/SSL to prevent interception and ensure authentication data remains confidential and tamper-proof.
4. Integrate Multi-Factor Authentication (MFA)
Enhance security by adding an extra layer of verification, such as one-time passwords (OTPs), biometric scans, or hardware tokens. Adaptive MFA can assess login risks and prompt additional authentication when unusual activity is detected, reducing unauthorized access while maintaining a seamless user experience. Businesses that hire remote developers can especially benefit from these measures, ensuring secure access to critical systems from various locations.
5. Establish Session and Token Management
Use secure session handling techniques, such as short-lived tokens, refresh tokens, and automatic session expiration. Implement mechanisms to prevent session hijacking, such as HTTP-only and secure cookies. Regularly validate and refresh authentication tokens to maintain security without requiring frequent re-authentication.
6. Monitor and Maintain Authentication Security
With the help of a dedicated development team, you can continuously track authentication logs to detect anomalies, failed login attempts, and potential security breaches.
Conduct regular security audits, update authentication systems to patch vulnerabilities, and educate users on safe authentication practices. Implement real-time alerts for suspicious activities to prevent unauthorized access.
Your Website’s Security Shouldn’t be An Afterthought
Let’s build a rock-solid web authentication system that protects your business and gives users peace of mind.
Conclusion
Implementing strong web authentication is crucial for safeguarding digital platforms. Businesses can reduce vulnerabilities and enhance user trust by adopting secure authentication methods, enforcing best practices, and leveraging protocols like FIDO2 and OAuth.
Continuous monitoring, regular updates, and adaptive authentication strategies help maintain long-term security. As authentication technology advances, organizations must stay ahead of emerging threats by adopting innovative, scalable, and user-friendly solutions to protect their systems and data effectively.
FAQs
Authentication verifies that a user, system, or device is who they claim to be. It acts like a digital bouncer, checking credentials (like passwords or biometrics) before granting access. Without it, anyone could waltz in and mess with sensitive data or accounts.
Web form authentication is when a website asks for a username and password through a login form. If the credentials match what’s stored in the system, access is granted. It’s the standard way most sites verify users before letting them in, from email accounts to shopping platforms.
User authentication is the process of confirming a person’s identity before allowing access to an account, app, or system. User authentication techniques involve passwords, PINs, biometrics, or security codes. Think of it as your digital ID check—no valid proof, no entry.
Authentication can be done using passwords, fingerprint scans, one-time codes, or multi-factor authentication (MFA). The stronger the method, the safer your account. A good habit? Use unique passwords and enable MFA whenever possible—because hackers love lazy authentication mechanisms.
The best authentication depends on security needs. For basic sites, password-based logins work. For stronger security, multi-factor authentication (MFA) or biometrics (fingerprint, face ID) are better. Businesses often use Single Sign-On (SSO) or OAuth to make access seamless without compromising security.
Talk With Our Expert
Our Latest Insights
USA
2102 Linden LN, Palatine, IL 60067
+1-703-537-5009
[email protected]
UK
Debut Infotech Pvt Ltd
7 Pound Close, Yarnton, Oxfordshire, OX51QG
+44-770-304-0079
[email protected]
Canada
Debut Infotech Pvt Ltd
326 Parkvale Drive, Kitchener, ON N2R1Y7
+1-703-537-5009
[email protected]
INDIA
Debut Infotech Pvt Ltd
C-204, Ground floor, Industrial Area Phase 8B, Mohali, PB 160055
9888402396
[email protected]




Leave a Comment