Table of Contents
Home / Blog / Blockchain
How to Create a Permissioned Blockchain: A Step-by-Step Guide
January 15, 2025

January 15, 2025
Creating a permissioned blockchain offers businesses benefits such as enhanced security, efficiency, and a tailored solution that meets their specific needs. Statistics show that over 50% of all organizations adopting blockchain technology were turning to permissioned models instead of the full-access ones in 2018.
In addition, organizations can easily customize features to manage data, access control, and regulatory compliance, thanks to permissioned models.
With controlled transparency, improved scalability, and high security, businesses can create blockchain solutions that ensure efficient transactions, protect sensitive data, and support large-scale enterprise blockchain development and applications. This makes it ideal for various industries.
In this article, we will cover how to create a permissioned blockchain, its various benefits, and the challenges organizations may face when implementing it. We will also discuss real-world use cases.
Looking to create a permissioned blockchain for your business?
Let us guide you through every step, from design to deployment. Our team specializes in building secure, scalable, customized blockchain solutions tailored to your unique business requirements.
What is a Permissioned Blockchain?
A permissioned blockchain is a form of distributed ledger that restricts participant access to predefined entities. In contrast to public blockchains, where anyone can join and validate transactions, permissioned blockchains ensure that only authorized participants can engage in specific activities. These systems are designed to balance transparency and control, making them particularly suitable for enterprise-level applications where data privacy and governance are critical.
Permissioned blockchains offer enhanced security, operational efficiency, and scalability compared to their permissionless counterparts, while still leveraging the benefits of blockchain technology, such as immutability and decentralized data management.
Permissioned vs. Permissionless Blockchain
Before diving into how to create a permissioned blockchain, let’s look at a comparison between permissioned and permissionless blockchain:
1. Enterprise vs. Public Use
Permissioned blockchains cater to enterprises requiring controlled environments for data sharing and transactions.
Public blockchains, by contrast, are open networks designed for anyone to participate. This makes them ideal for decentralized apps and applications like cryptocurrencies.
Permissioned blockchains are more aligned with regulatory compliance. This makes them preferable for industries such as finance, healthcare, and supply chain management.
2. Decentralization
While permissionless blockchains emphasize full decentralization, permissioned blockchains strike a balance between decentralization and centralized control. Participants are vetted, and governance is often managed by a consortium or a central authority. This ensures accountability while maintaining some level of decentralization.
3. Development
Development processes for permissioned blockchains prioritize customization to meet specific organizational needs. When you hire Blockchain Developers, they can help design tailored features such as identity management systems, private channels, and bespoke consensus mechanisms to align with industry-specific requirements.
4. Transparency
Permissioned blockchains provide a controlled degree of transparency. While transaction records remain immutable, access to view or verify transactions can be restricted based on user roles. This ensures privacy and compliance with data protection regulations.
Types of Consensus Protocols for Permissioned Blockchain Networks
Here are the popular types of consensus protocols for permissioned blockchain networks:
1. Practical Byzantine Fault Tolerance (PBFT) Consensus:
PBFT is a robust consensus mechanism designed to handle up to one-third of faulty or malicious nodes. It relies on a leader-follower structure, ensuring transaction validation through multiple rounds of communication. This protocol is particularly suited for environments requiring high fault tolerance and consistent performance.
2. Federated Byzantine Agreement (FBA):
FBA enables consensus by leveraging trust within a subset of nodes, called a quorum slice. Each node independently selects its trusted nodes, creating overlapping quorum slices that collectively secure the network. FBA is highly scalable and is often used in systems prioritizing efficiency and low latency.
3. Round Robin Consensus
Round Robin consensus assigns transaction validation tasks sequentially among nodes. This method is straightforward and ensures equal participation in the consensus process. While not as fault-tolerant as PBFT, it is well-suited for networks with trusted participants.
4. RAFT
RAFT is a leader-based consensus mechanism that simplifies the consensus process by electing a leader node to manage transaction validation and ledger updates. It is highly efficient and easy to implement, making it ideal for permissioned blockchains with smaller networks.
Suppose you’re not certain of the consensus protocols to use. In that case, a reputable and top blockchain development company such as Debut Infotech can help guide you.
Benefits of Using Permissioned Blockchains
To understand why many organizations create a permissioned blockchain, let’s cover the benefits of using permissioned blockchains:
1. Easy Customization
Permissioned blockchains provide businesses with the flexibility to design customized solutions that address their unique needs.
Developers can modify the blockchain’s features to streamline data management, define access controls, and meet specific regulatory compliance requirements. This level of customization allows organizations to create tailored environments that align with their operational goals. In addition, it also ensures that the blockchain solution is optimal for their specific use case while maintaining a high level of security and efficiency.
2. Controlled Degree of Transparency
One of the primary advantages of blockchain permissioned is the ability to control the visibility of data within the network.
While transaction records remain immutable, organizations can selectively limit access to sensitive information, ensuring that only authorized parties can view or modify certain data. This controlled transparency builds trust among participants, guaranteeing that information is secure. It also prevents the exposure of confidential details to unauthorized entities. This fosters a secure and reliable environment for collaboration.
3. Efficiency
Permissioned blockchains are designed to maximize efficiency by optimizing consensus mechanisms and restricting participant access.
With fewer nodes involved in transaction validation, the network can process transactions faster compared to permissionless blockchains. This increased transaction throughput significantly reduces operational costs. Because of this, businesses do not need to invest in the heavy computational power required by public blockchain systems.
As a result, organizations benefit from improved transaction speed and reduced time-to-market. This drives operational efficiency and cost-effectiveness.
In the long run, it’ll be evident that the blockchain development cost and expenses associated with creating a permissioned blockchain are worth it.
4. Scalability
The scalability of permissioned blockchains makes them ideal for large-scale enterprise applications. By limiting participation and using optimized blockchain ecosystem protocols, these blockchains can manage growing transaction volumes and larger networks with ease.
The ability to scale effectively allows organizations to expand their operations without compromising performance or security. Whether accommodating more participants or processing an increasing number of transactions, permissioned blockchains provide a reliable foundation for businesses looking to grow while maintaining system integrity and performance.
5. Access
With permissioned blockchains, multi-level access control is implemented to ensure that only authorized individuals or entities can execute specific operations. This selective access ensures the security and integrity of the network by limiting exposure to sensitive data and restricting who can validate transactions or modify records. The ability to define roles and permissions for different participants enhances governance and provides granular control over operations. It also ensures that only trusted parties are involved in critical processes, thereby bolstering operational security.
6. High Security
Security is a major strength of permissioned blockchains. This is because they employ robust encryption techniques and restrict network access to authorized participants only.
Since people who can join the network and perform transactions are controlled, the system reduces the risk of malicious activities, fraud, and unauthorized data access. These security measures help safeguard sensitive information from external threats and ensure that only trusted parties can validate and record transactions. At the end of the day, this provides a secure environment for data storage and transaction processing.
Use Cases of Permissioned Blockchains
Here are the real-life use cases of permissioned blockchains:
1. Supply Chain Management
Permissioned blockchains enhance the transparency and traceability of supply chain management by producing an immutable record of transactions and product movements. Businesses can verify authenticity, streamline logistics, and improve trust among stakeholders. This technology also aids in reducing fraud and ensuring product quality through end-to-end visibility.
2. Healthcare
In healthcare, permissioned blockchains securely store and share patient records. This ensures data privacy and compliance with regulations like HIPAA. They facilitate interoperability between providers, enhancing care coordination and patient outcomes.
Additionally, these blockchains streamline clinical trials by securely managing data and improving collaboration between stakeholders.
3. Financial Services
Financial institutions use permissioned blockchains to streamline processes such as cross-border payments, trade finance, and identity verification. These systems reduce fraud, enhance transaction speeds, and improve regulatory compliance. Permissioned blockchains also provide a secure framework for managing contracts and settlements. This boosts overall efficiency.
4. Government Services
Governments leverage permissioned blockchains for secure and transparent management of public records, such as land registries and identity documents. These systems help reduce corruption, enhance data integrity, and streamline administrative processes. As it offers a tamper-proof record, this helps to improve trust between citizens and government bodies.
Challenges of Permissioned Blockchains
Here are some challenges associated with permissioned blockchain:
1. Centralization Risks
Despite their enhanced security features, blockchain permissioned can lead to centralization concerns. Since only authorized entities control access, there is a risk that a few parties may hold too much control over the network. This centralized structure may undermine the very decentralized principles that blockchain technology aims to promote and limit its full potential for transparency and trust.
2. Scalability Issues
Scalability remains a significant challenge for permissioned blockchains. The need for frequent validation of transactions by trusted entities can slow down processing speeds as the network grows. This limitation makes it difficult to handle high-volume transactions. This is quite common in industries such as finance or supply chain management, where speed and efficiency are crucial.
Improving scalability requires further technological innovations and optimizations.
3. Interoperability Challenges
Interoperability between different permissioned blockchain systems is another challenge. As different organizations and sectors implement their blockchain solutions, ensuring seamless communication and data exchange between these diverse systems becomes difficult.
Without effective interoperability, the value of a permissioned blockchain system may be limited. This will prevent widespread adoption.
Developing industry-wide standards and protocols is essential for enhancing interoperability and fostering collaboration across sectors.
Comprehensive Guide to Creating a Permissioned Blockchain
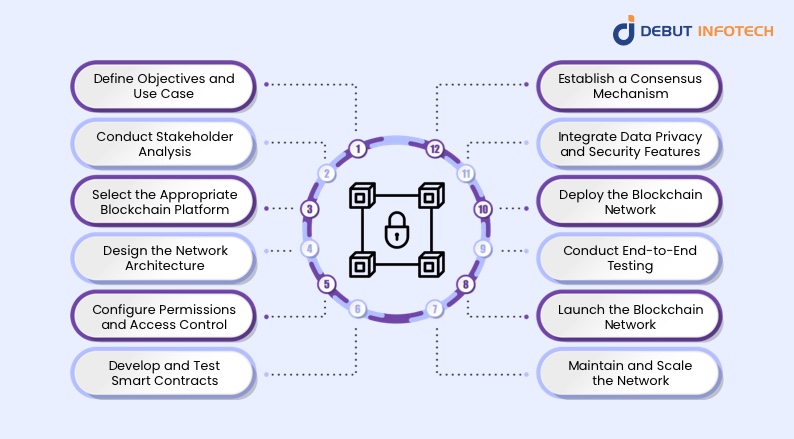
Building a blockchain permissioned is a complex task that requires careful design, technical knowledge, and an understanding of the particular needs and limitations of the intended use case.
Here is a step-by-step guide on how to create a permissioned blockchain:
Step 1: Define Objectives and Use Case
Begin by defining the objectives of your permissioned blockchain. Identify the specific problems it will solve, the stakeholders involved, and the type of data it will manage. Establish clear use cases, whether for supply chain management, financial services, or healthcare. This ensures alignment among all parties and a roadmap for blockchain business development. Factor in potential scalability, compliance requirements, and long-term goals to create a solution that adapts as your needs evolve.
Step 2: Conduct Stakeholder Analysis
Map out all stakeholders who will interact with the blockchain. This includes businesses, regulators, and end-users. Document their roles, concerns, and expectations. Use stakeholder interviews and workshops to gather detailed insights. This analysis informs the design of the network, ensuring it addresses all relevant needs. Clear communication with stakeholders fosters trust and smooth adoption, laying the groundwork for successful implementation.
Step 3: Select the Appropriate Blockchain Platform
Evaluate blockchain platforms based on your use case. Consider options like Hyperledger Fabric for modular architecture, Corda for transaction privacy, and Quorum for Ethereum compatibility with added privacy. Assess performance metrics, community support, integration capabilities, and cost. Selecting the right platform is crucial to achieving efficiency and scalability. A thorough evaluation minimizes technical challenges and ensures the platform meets your operational requirements.
Step 4: Design the Network Architecture
Plan a comprehensive network architecture. Define the number and placement of nodes, their responsibilities, and how they communicate.
Choose a consensus mechanism suitable for permissioned networks, such as Practical Byzantine Fault Tolerance (PBFT) or Raft.
Create a governance framework for decision-making and conflict resolution. A robust architecture ensures high performance, fault tolerance, and clarity in managing network operations.
Step 5: Configure Permissions and Access Control
Develop a detailed access control framework. Assign roles and permissions for each participant, ensuring only authorized users can access specific data or functions.
Use identity verification methods like digital certificates and PKI (Public Key Infrastructure). Implement governance rules for onboarding and removing participants. Strong permissions ensures data security and operational integrity, which is critical for building trust within the network.
Step 6: Develop and Test Smart Contracts
Design smart contracts to automate and enforce business logic. Use platform-specific languages like Solidity for Quorum or Chaincode for Hyperledger. Ensure contracts are transparent and aligned with legal and regulatory requirements. Rigorously test smart contracts through unit and blockchain integration tests to eliminate bugs and vulnerabilities. Well-crafted smart contracts increase operational efficiency and reduce human error, making the blockchain more reliable.
Step 7: Establish a Consensus Mechanism
Choose and configure a consensus algorithm that aligns with the network’s needs. For instance, Proof of Authority (PoA) works well for high-efficiency networks, while PBFT ensures fault tolerance. Define parameters such as block times and validation rules. Test the mechanism in different scenarios to confirm its stability and performance. A robust consensus process ensures transaction validity and network reliability.
Step 8: Integrate Data Privacy and Security Features
Implement privacy and security measures to safeguard sensitive information. Use encryption techniques for data at rest and in transit. Establish secure communication protocols, such as TLS. Introduce periodic security audits and penetration testing to identify vulnerabilities. Additionally, consider regulatory compliance for data protection laws like GDPR. These measures are critical to maintaining trust and ensuring data confidentiality within the blockchain.
Step 9: Deploy the Blockchain Network
Set up nodes and deploy the network. Install and configure node software on designated servers. Establish peer-to-peer connections for seamless data flow.
Deploy the governance framework, consensus mechanism, and smart contracts. Perform deployment tests to identify and address potential issues before the system goes live. A smooth deployment process minimizes downtime and ensures network readiness.
Step 10: Conduct End-to-End Testing
Perform comprehensive testing of the blockchain system. Stress test the network under high transaction volumes to assess its performance. Conduct vulnerability assessments to identify and mitigate cybersecurity risks. Test integrations with existing systems, ensuring seamless data exchange. User acceptance testing (UAT) confirms that the system meets stakeholder requirements. Rigorous testing ensures a secure, functional, and user-friendly blockchain.
Step 11: Launch the Blockchain Network
Roll out the blockchain in a controlled environment before full-scale production. Offer training sessions for users to familiarize them with the system. Monitor the network for unexpected behavior during the initial phase. Gather feedback from participants to address any operational issues promptly. A phased launch reduces risk and builds confidence among users, ensuring smooth adoption. If you’re stuck at any point, experienced blockchain consultants can guide you through this phase.
Step 12: Maintain and Scale the Network
Regularly monitor the network to identify performance bottlenecks and security vulnerabilities. Update software and configurations as needed to enhance functionality. Plan for scalability by adding nodes, upgrading consensus algorithms, and introducing new features based on user feedback. Proactive maintenance ensures the network remains efficient, secure, and capable of meeting evolving demands.
Ready to unlock the potential of permissioned blockchain technology?
Partner with our experts to design, develop, and implement a solution that prioritizes security, control, and performance. Whether you’re managing sensitive data or streamlining operations, we’ll help you achieve your goals with confidence.
Conclusion
Permissioned blockchains provide a practical and balanced solution to leveraging the benefits of blockchain technology in scenarios where data privacy, security, and control are essential. Understanding their use cases and features can help organizations discover how to use their potential to drive innovation and efficiency across multiple industries.
It’s crucial to understand that building a permissioned blockchain is a complex process that requires strategic planning and technical expertise. However, following the 12 steps outlined can help you create a permissioned blockchain tailored to your organization’s needs.
FAQs
Permissioned blockchains typically use consensus algorithms like Practical Byzantine Fault Tolerance (PBFT), Raft, or Proof of Authority (PoA). These are designed for trusted environments, ensuring faster and more efficient decision-making compared to public blockchain algorithms like Proof of Work (PoW).
Permissioned blockchains face issues like scalability limits, centralized control concerns, and interoperability challenges with other networks. Managing participant trust and maintaining a balance between transparency and privacy can also be tricky.
Designing a permissioned blockchain involves addressing trust models, participant authentication, data access control, and scalability. It’s crucial to ensure efficient consensus while keeping the system secure and user-friendly for enterprise needs.
A consortium blockchain is a type of permissioned blockchain managed by a group of organizations, not a single entity. Permissioned blockchains, in general, restrict access but can be controlled by either a single organization or multiple entities like in a consortium setup.
Permissioned blockchains control participation through strict access rules. Participants need approval, often verified by digital certificates or pre-set identity protocols, ensuring only trusted entities can join and interact in the network.
Talk With Our Expert
USA
2102 Linden LN, Palatine, IL 60067
+1-708-515-4004
info@debutinfotech.com
UK
Debut Infotech Pvt Ltd
7 Pound Close, Yarnton, Oxfordshire, OX51QG
+44-770-304-0079
info@debutinfotech.com
Canada
Debut Infotech Pvt Ltd
326 Parkvale Drive, Kitchener, ON N2R1Y7
+1-708-515-4004
info@debutinfotech.com
INDIA
Debut Infotech Pvt Ltd
Sector 101-A, Plot No: I-42, IT City Rd, JLPL Industrial Area, Mohali, PB 140306
9888402396
info@debutinfotech.com




Leave a Comment