Table of Contents
Home / Blog / Cryptocurrency
Best Strategies For Secure Crypto Wallet in Business Applications
October 7, 2024

October 7, 2024
More companies are realizing the necessity for secure crypto wallet development as the use of cryptocurrencies increases in order to manage and protect their digital assets. Businesses have to give security first priority, whether they are using it for internal purposes or providing wallet services to consumers to help reduce the dangers connected with crypto transactions. A poorly designed wallet could reveal private financial information and cause terrible losses. Given the growing volume of digital assets transferred and kept, crypto security is now more important than ever.
Any ecosystem for cryptocurrencies depends on crypto wallets absolutely. They let consumers securely save, receive, and move digital currencies. However, developing these wallets requires a thorough knowledge of blockchain technology and the capacity to predict and minimize the possible hazards related to managing digital currencies. The stakes are significantly higher for companies as the wallets they create have to guard not only the business’s assets but also those of their customers.
The key tactics companies should use to guarantee the security and functionality of their cryptocurrency wallets will be discussed in this blog. We will explore wallet development costs, crypto wallet security, cryptocurrency security concerns, and how wallets could create income. We will also stress important technologies that might greatly improve wallet security and functionality: MPC crypto wallet and crypto trading bot development.
Ready to build a secure, reliable cryptocurrency wallet for your business?
Our knowledgeable staff specializes in Crypto Wallet Development. From bespoke white label solutions to blockchain wallet development, we enable you to keep ahead of the always changing crypto scene.
Understanding Cryptocurrency Security in Wallet Development
Cryptocurrency security is the core of secure wallet development. Because of its decentralized qualities, cryptocurrencies run without middlemen, unlike banks. Hence users and wallet creators have the whole responsibility for security. Unlike conventional banking systems, where money is guaranteed or protected by government-owned companies, cryptocurrencies offer no such security net. Thus, it is absolutely important to guarantee the security of the wallet handling these valuables.
Companies who create wallets have to be aware of the main security concerns involving cryptocurrencies. These cover phishing campaigns, malware, hacking efforts, and inadequate encryption standards. All of these hazards could result in illegal wallet access, risking client money and corporate assets.
Types of Crypto Wallets
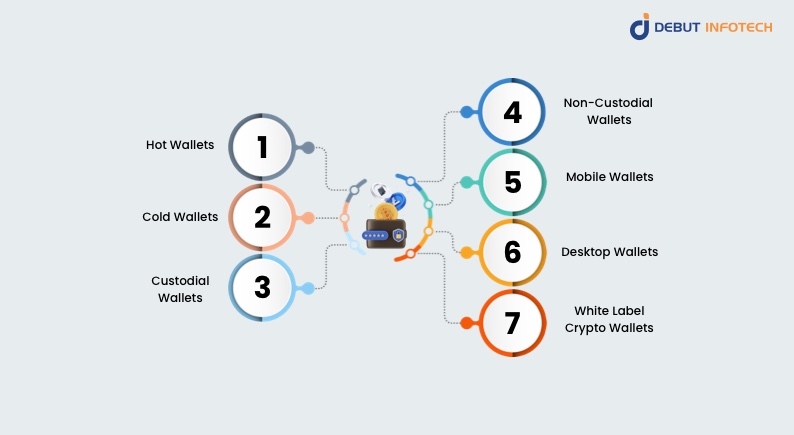
There are numerous kinds of wallets accessible when it comes to cryptocurrencies. Each with varied uses and degrees of security value. Businesses choosing which wallet to create or use depends on an understanding of these different types of wallets.
- Hot Wallets: Usually used for daily purchases, hot wallets are linked to the internet and are more prone to hacks and cyberattacks, even if they are convenient and user-friendly.
- Cold Wallets: Cold wallets are offline storage options. Since they are not linked to the internet, they are considered the safest place to store cryptocurrency long-term. Two such are paper wallets and hardware wallets.
- Custodial Wallets: Custodial wallets are those that hold the private keys on behalf of the user, therefore giving the wallet provider authority over the keys. For those who might not be tech-savvy, this can be handy; but it adds a single point of failure as the provider might be hacked.
- Non-Custodial Wallets: Non-custodial wallets provide consumers total control over their private keys, therefore improving security and privacy. This means, nonetheless, that users must make keeping their keys safe their own responsibility.
- Mobile Wallets: Designed for smartphones, mobile wallets offer a handy approach to keep and manage cryptocurrencies. Although they are easy to use, phishing attacks and malware might find their way in them.
- Desktop Wallets: Desktop wallets are software programs housed on a desktop computer. They strike a mix between convenience and security, but should the computer be hacked they might be exposed.
- White Label Crypto Wallets: These pre-built solutions let companies enter the market fast by customizing their branding and functionality. Still, it’s important to make sure these wallets satisfy rigorous security criteria.
Key Components of Secure Crypto Wallets
There are few elements companies have to include into a secure wallet to protect assets. These characteristics are essential to provide a safe crypto wallet that guards against the several security concerns related to the realm of digital assets.
- Private Key Management: This is essentially the cornerstone of wallet security. Access to cryptocurrency comes via private keys. Should the wallet be breached, the attacker might take complete control of what is stored inside. Companies have to make sure private keys are never displayed in plaintext and are kept safely. By distributing private keys among several parties, techniques include multi-signature (multisig) authorisation and MPC wallets can provide further degrees of security.
- Multi-Signature Authorization: Multisig wallets offer increased security by mandating several signatures to authorize a transaction. This guarantees that the funds stay safe even in case one private key is hacked, as a transaction cannot be handled without other signatures.
- Encryption and Secure Coding Practices: Strong encryption techniques are absolutely necessary for wallet data security via safe coding practices. User data and transaction data, should be encrypted by developers using tried-upon cryptographic techniques. Furthermore, lowering the possibility of hacks and breaches are safe coding techniques like periodic security audits and minimum of code vulnerabilities.
- Two-Factor Authentication (2FA): Two-factor authentication (2FA) is a straightforward yet powerful method of adding an additional layer of protection to wallets. Users must present two types of identification: usually something they know—a password—and something they own—a cell phone with an authenticator software.
- Cold Storage Solutions: Using cold wallets—offline wallets—is quite advised for long-term crypto storage. Cold wallets hold assets offline, therefore shielding them from online dangers, unlike hot wallets, which are linked to the internet and more prone to hacking.
Wallet Security Best Practices
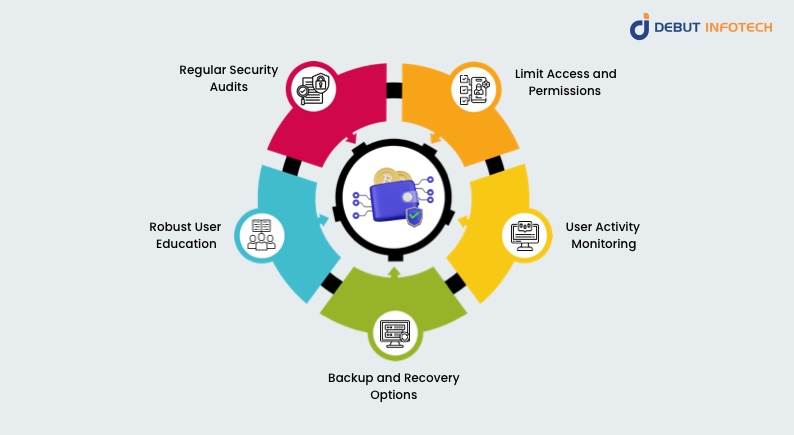
Using recommended practices during wallet development will greatly improve security and help to guard against possible hazards. These are some essential elements to incorporate:
- Regular Security Audits: Identification and correction of wallet vulnerabilities depend on regular security audits. Assessments should be conducted thorough by outside security professionals.
- Robust User Education: Teaching consumers about best practices for wallet security will help to reduce risks. Giving consumers clear directions on spotting phishing attempts and locking their private keys would help them to guard their belongings.
- Backup and Recovery Options: It is absolutely imperative to have strong backup and recovery mechanisms. Should devices be lost or stolen, users should be able to quickly retrieve their wallets. Make sure recovery choices are safe yet also easy for usage.
- User Activity Monitoring: Using monitoring tools will enable one to find unusual or illegal conduct. Should suspect behavior come across, users can be notified and transactions might be temporarily stopped for inspection.
- Limit Access and Permissions: Limit user rights depending on their roles when you create the wallet. This guarantees that only authorized users may use wallet sensitive features.
Choosing the Right Crypto Wallet Type for Business
Depending on their size and scope of business, companies have distinct needs for wallet development. Choosing the correct kind of wallet is vital whether their intended use is for internal use or they intend to sell one to their clients.
- Custodial vs Non-Custodial Wallets: Custodial wallets offer the wallet provider authority over users’ private keys, therefore contrasting with non-custodial wallets. For companies who provide wallet services to customers, this can be helpful since it lets them get money back. Though it lays all the responsibility of security entirely on the user, non-custodial wallets provide users complete control over their keys, therefore providing more privacy and security.
- White Label Crypto Wallets: Using a white label crypto wallet could be a good choice for companies looking to join the market fast. One can personalize these pre-built wallet solutions with features and branding of a business. Although faster to implement, companies have to make sure the white-label solution they choose follows the best security guidelines.
How Crypto Wallets Make Money
Understanding how crypto wallets make money is key to the business value they provide. Not only do wallets help with transactions; they can also bring income from several sources:
- Transaction Fees: One of the most often used methods wallets earn money is by use of transaction fees. The business can collect a little charge each time a user transmits cryptocurrency through the wallet.
- Staking Services: Certain wallets include staking services for Proof-of- Stake coins. The wallet provider earns a fee on the rewards while users lock their money in the wallet and get benefits.
- Exchange Integration: Many wallets have crypto exchanges so users may purchase and sell straight from the wallet. By taking a portion of every trade, wallets can provide income.
- Premium Features: For a price some wallets provide faster transaction processing or improved security. For the wallet provider, this can give still another source of income.
Costs Associated with Crypto Wallet Development
The features, security methods, and scalability needs of a developing secure crypto wallet affect the associated expenses. Businesses should take these elements into account while planning for crypto wallet development:
- Development Expenses: The complex structure of the wallet directly affects development expenses. Advanced feature wallets with cold storage options, MPC wallets, or multi-signature authorisation will demand more resources and result in additional development expenses.
- Security Implementation: Including strong security elements like regular security audits and encryption will greatly affect the crypto wallet development cost. For companies trying to safeguard their assets and prevent the financial damages related to breaches, this is a non-negotiable cost nonetheless.
- Maintenance and Updates: Following the first development phase, companies have to keep updating their wallets to keep ahead of new risks and increase functionality. Maintaining wallets safe over long terms depends on routine security audits and software updates.
Blockchain Wallet Development and Its Role
The best crypto wallets, companies are progressively depending on blockchain wallet development to provide transparent and safe financial transactions. A blockchain wallet lets users engage with several blockchains, therefore enabling the sending and receiving of cryptocurrency across several networks. Development of a blockchain wallet calls for a thorough knowledge of blockchain protocols and security criteria, so it is more difficult than development of a regular crypto wallet.
Crypto Wallets vs. Exchanges: A Comparison
Regarding the management of digital resources, companies sometimes have to decide between a crypto wallet vs exchange. Although both help to control assets, their security and use differ greatly.
Crypto wallets provide companies direct control over their private keys, therefore enhancing security and privacy. Still, they usually demand more of the user as losing a private key means the irreversible loss of money.
Exchanges oversee the storage and transaction of cryptocurrencies, therefore serving as middlemen. Although handy, they are more prone to hacks since centralized locations house a lot of assets.
The particular requirements of a company and its attitude to security will determine which of a crypto wallet or exchange best fits them.
Key Technologies Enhancing Wallet Security
Many developing technologies are significantly helping companies to enhance wallet security. Some of them are:
- MPC Wallets:Multi-party computation (MPC) wallets allow private keys to be divided across several machines, therefore lowering the single point of failure risk. Those companies trying to improve crypto wallet security have grown especially fond of this technology.
- TRC20 Wallets: TRC20 wallets are becoming more popular as companies search for scalable, more safe blockchain systems. Designed on the Tron blockchain, TRC20 crypto wallets are a safe choice for companies handling significant transaction volume since they are fast and low fee based.
- XDC Crypto: Another blockchain solution that has attracted companies using hybrid blockchain technology for both public and private blockchain transactions is the XDC network. For business-level transactions, XDC-based wallets offer a further degree of security and openness that appeals.
eWallet App Development and Cryptocurrency Trading Bots
Beyond traditional wallets, companies are also funding ewallet app development and crypto trading bot creation to increase their range of cryptocurrencies offered. While cryptocurrency trading bots let companies automate trading plans, therefore optimizing productivity and profit, eWallets offer mobile-friendly alternatives for handling cryptocurrencies.
Have questions or need a custom crypto wallet for your business?
We’re here to help. Contact us to discuss your specific needs, and let our team of blockchain experts guide you through every step of the development process.
Conclusion
For companies wishing to enter the crypto wallet development market, security has to be the first priority. Understanding the natural security risks associated with cryptocurrencies and applying the above mentioned best practices will help companies make sure their wallets not only satisfy high security criteria but also offer a flawless user experience. Businesses have many options to build a safe crypto wallet that safeguards their assets and supports their expansion in the digital economy whether through blockchain wallet development, integrating advanced features like MPC wallets, or investigating new technologies such as TRC20 wallets, the possibilities are vast.
Debut Infotech, a leading cryptocurrency wallet development company, plays a pivotal role in this space, offering tailored wallet development solutions designed to address both security and usability. We leverage our expertise in blockchain wallet development and cutting-edge technologies to help businesses safeguard their digital assets and scale efficiently. Our solutions ensure that businesses not only meet the highest security benchmarks but also benefit from a smooth user experience, positioning them for long-term success in the digital economy.
Frequently Asked Questions
The most common cryptocurrency security risks include hacking, phishing attacks, malware infections, and poor private key management. Without proper security measures such as encryption, two-factor authentication (2FA), and multi-signature authorization, wallets are vulnerable to unauthorized access. Regular security audits and updates are essential to mitigating these risks.
A hot wallet is connected to the internet, making it more convenient for daily transactions but more susceptible to hacking and other online threats. In contrast, a cold wallet is an offline storage solution that provides superior security, making it ideal for long-term storage of large cryptocurrency holdings. Cold wallets are generally less vulnerable to cyberattacks since they aren’t connected to the internet.
To ensure strong crypto wallet security, prioritize features like private key encryption, two-factor authentication (2FA), multi-signature (multisig) authorization, and regular security audits. Additional layers like MPC (multi-party computation) wallets and cold storage options also enhance security. Wallets should also offer backup and recovery options and real-time monitoring for unusual activity.
Businesses can choose from several types of crypto wallets based on their needs:
* Hot wallets offer quick, online transactions
* Cold wallets provide the best security with offline storage.
* Custodial options let providers manage private keys.
* Non-custodial choices grant users full control of their private keys.
* White-label crypto wallets offer customizable solutions for businesses looking to quickly launch branded wallets. Each type differs in security and user control.
Crypto wallet development costs depend on the wallet’s complexity, the security features implemented, and ongoing maintenance. Wallets with advanced features like multi-signature authorization, encryption, and MPC wallets will have higher development costs. Additionally, businesses must budget for regular updates, security audits, and compliance with evolving regulations to maintain wallet security over time.
Businesses can ensure user privacy by employing strong encryption for private keys and transaction data. Developing non-custodial wallets gives users full control over their private keys, enhancing privacy. Moreover, businesses should adopt secure coding practices and avoid storing sensitive information on centralized servers to minimize the risk of data breaches.
Crypto wallets can generate revenue through various methods, including transaction fees, integration with cryptocurrency exchanges, offering premium features like enhanced security, and providing staking services where users can earn rewards. Additionally, businesses may charge for specific functionalities or offer white label crypto wallets to other companies for a fee, allowing them to brand and use the wallets for their customers.
Talk With Our Expert
Our Latest Insights
USA
2102 Linden LN, Palatine, IL 60067
+1-703-537-5009
[email protected]
UK
Debut Infotech Pvt Ltd
7 Pound Close, Yarnton, Oxfordshire, OX51QG
+44-770-304-0079
[email protected]
Canada
Debut Infotech Pvt Ltd
326 Parkvale Drive, Kitchener, ON N2R1Y7
+1-703-537-5009
[email protected]
INDIA
Debut Infotech Pvt Ltd
C-204, Ground floor, Industrial Area Phase 8B, Mohali, PB 160055
9888402396
[email protected]




Leave a Comment